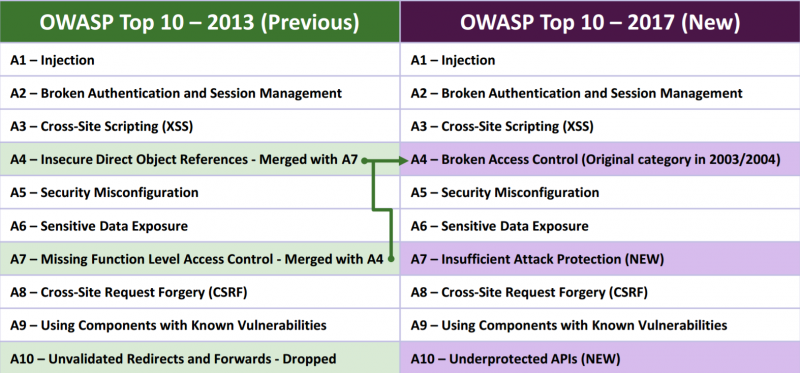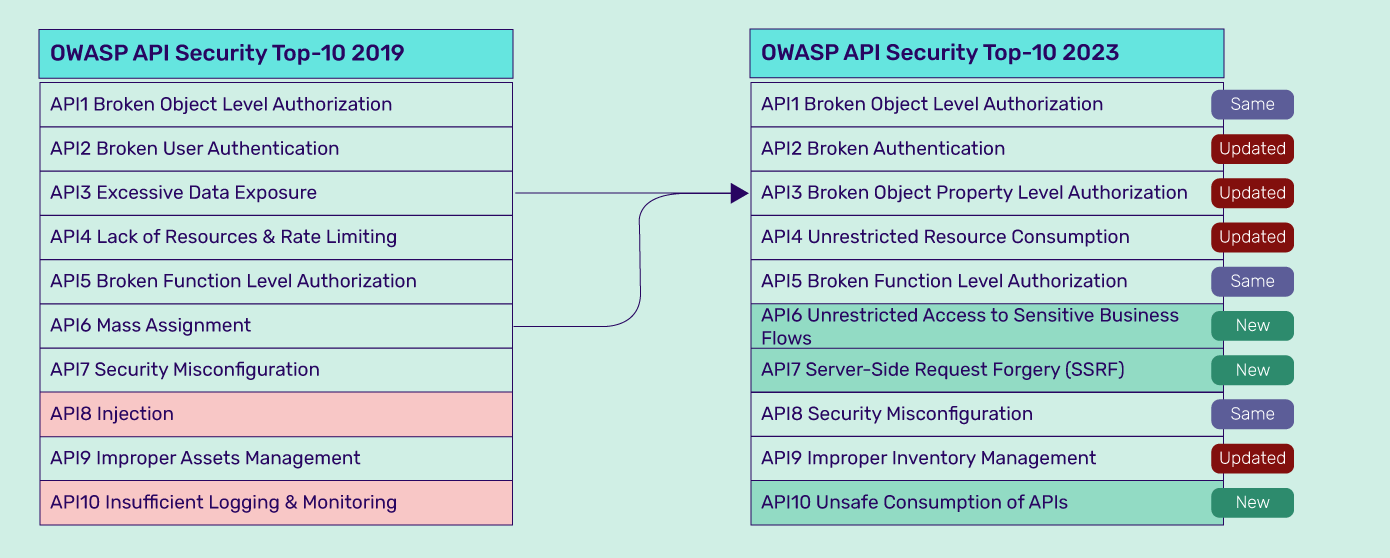
PDF) Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST)
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/6-Figure4-1.png)
PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar
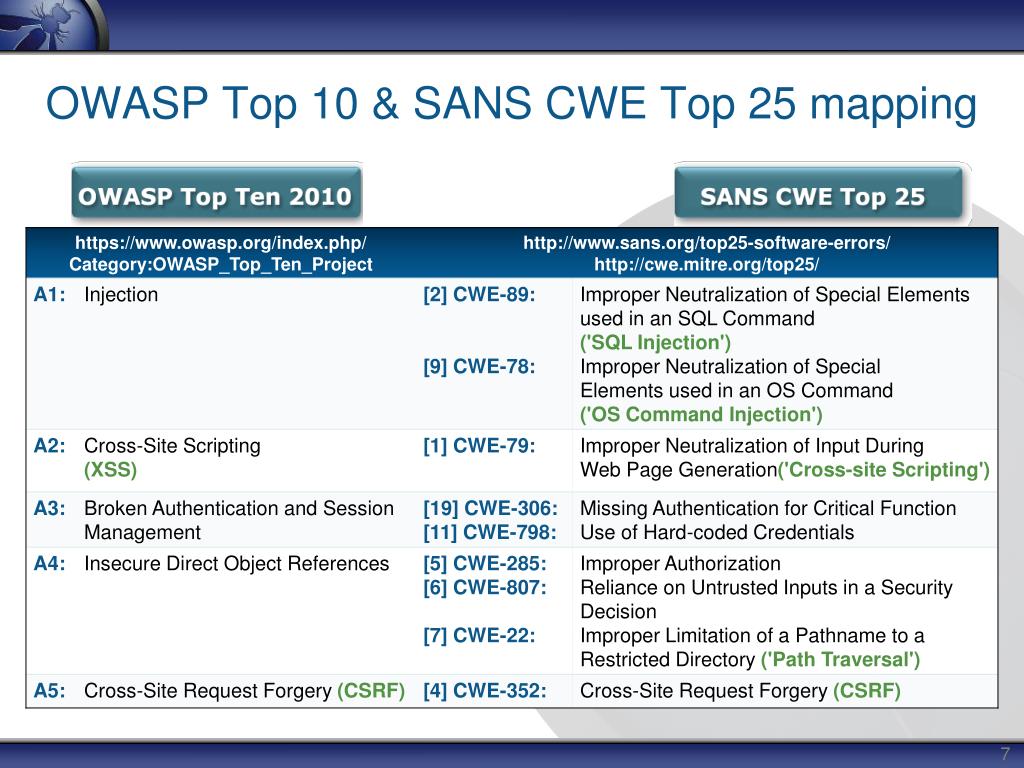
PPT - 2010 CWE/SANS Top 25 with OWASP Top 10 and PCI DSS V2 Mapping PowerPoint Presentation - ID:5764950
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/4-Table1-1.png)
.jpg)