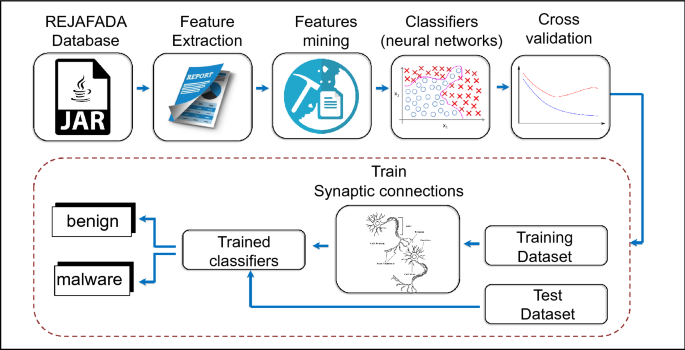
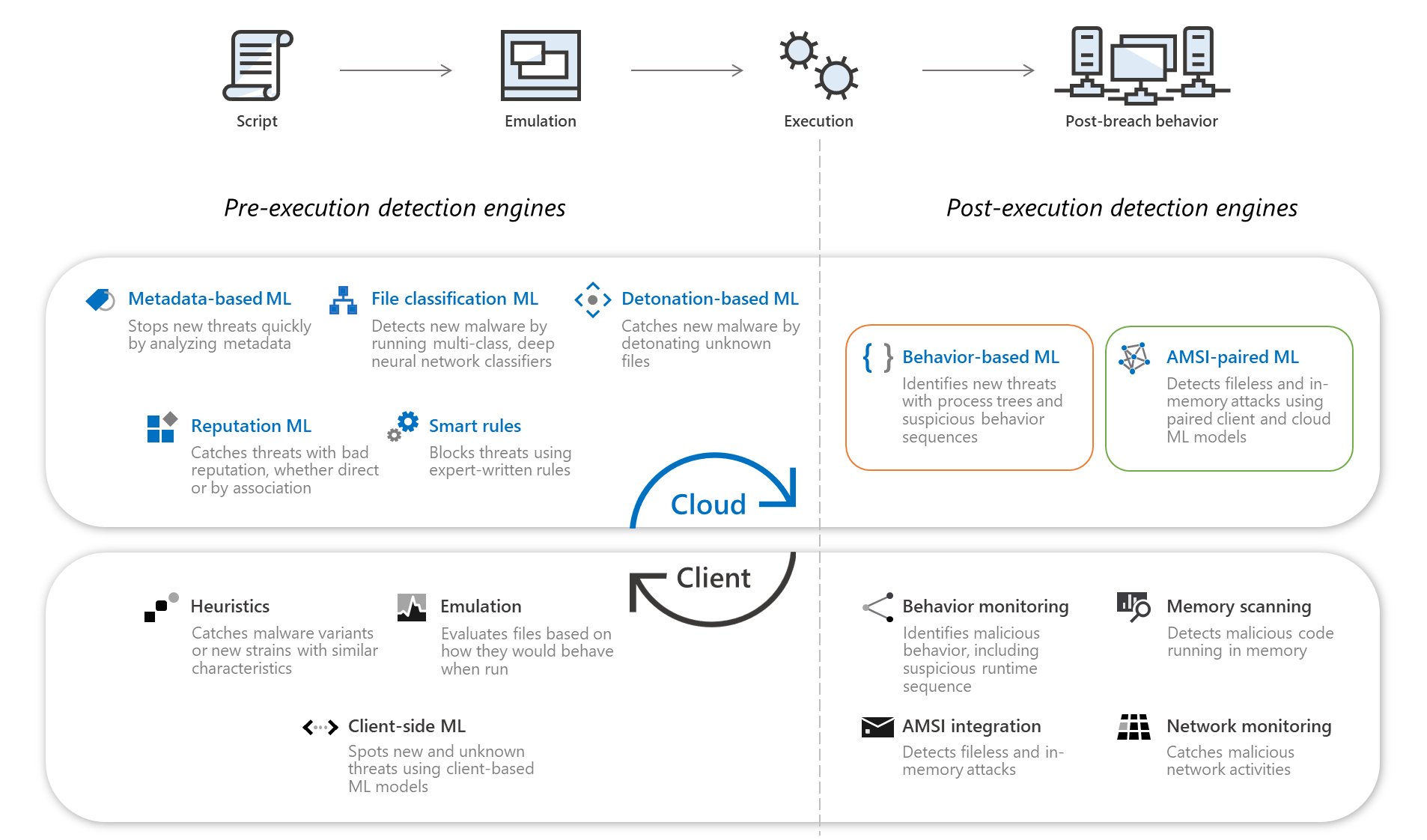
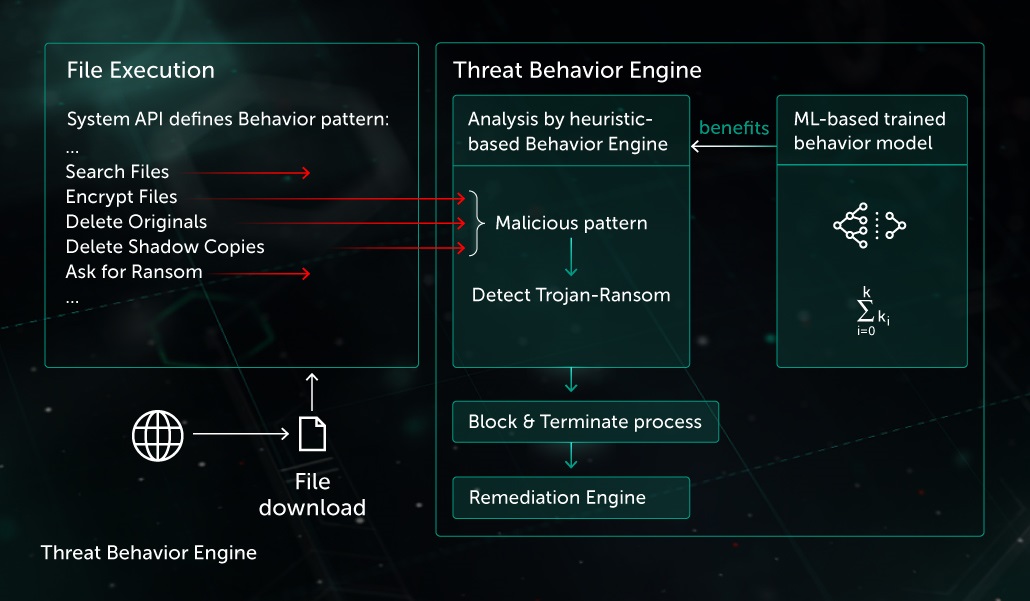
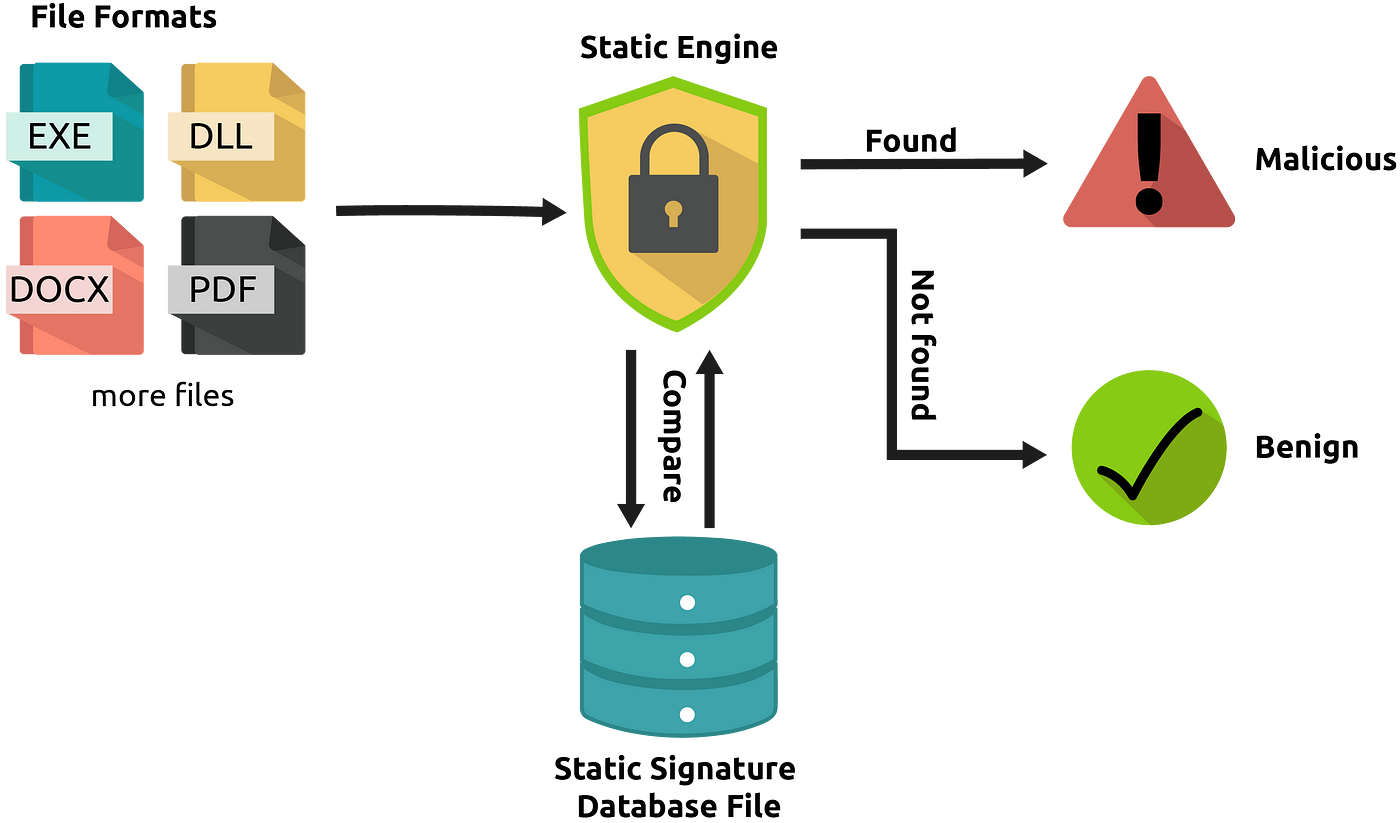
In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks | Microsoft Security Blog

What Is Network Behavior Anomaly Detection? Definition, Importance, and Best Practices for 2022 - Spiceworks

In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks | Microsoft Security Blog

In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks | Microsoft Security Blog