
Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign | Microsoft Security Blog

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud | Microsoft Security Blog

JCP | Free Full-Text | Business Email Compromise (BEC) Attacks: Threats, Vulnerabilities and Countermeasures—A Perspective on the Greek Landscape

Business Process Compromise, Business Email Compromise, and Targeted Attacks: What's the Difference? - Security News

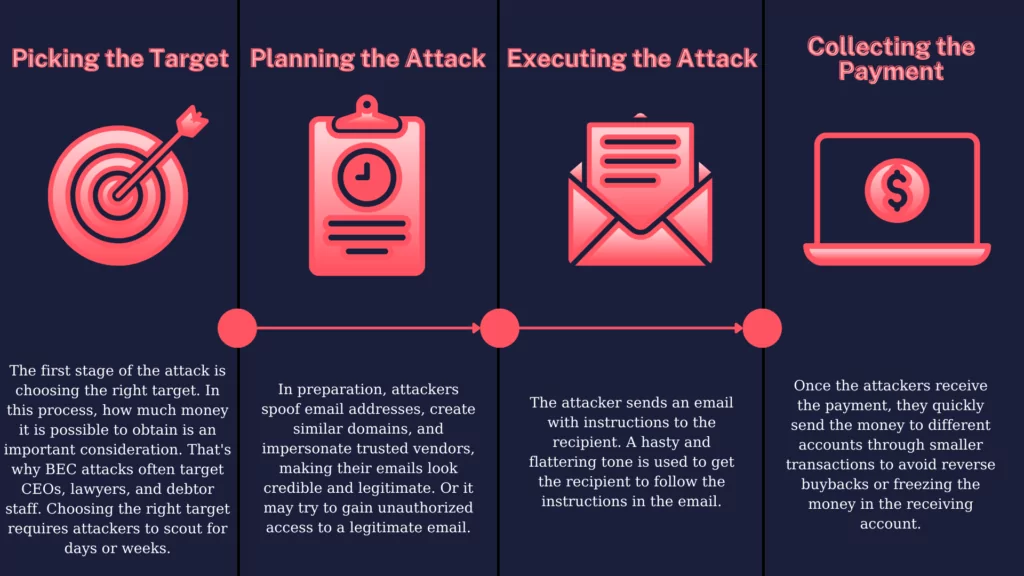
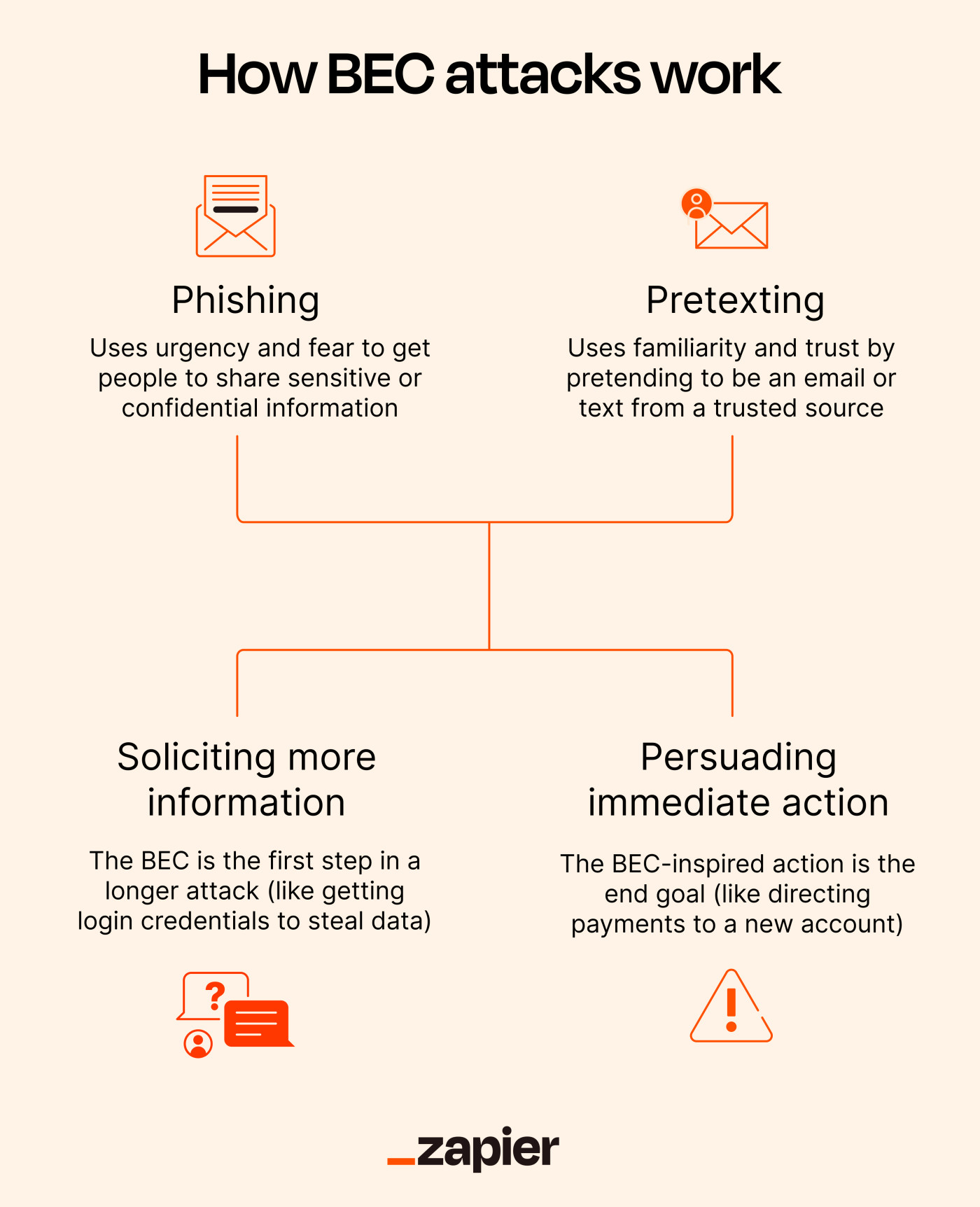

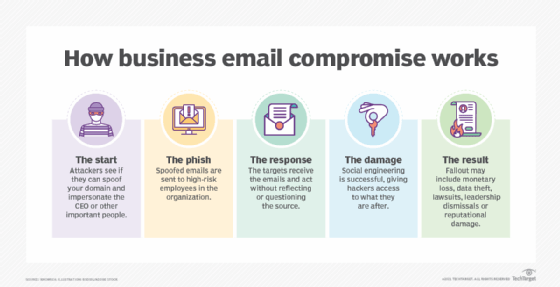





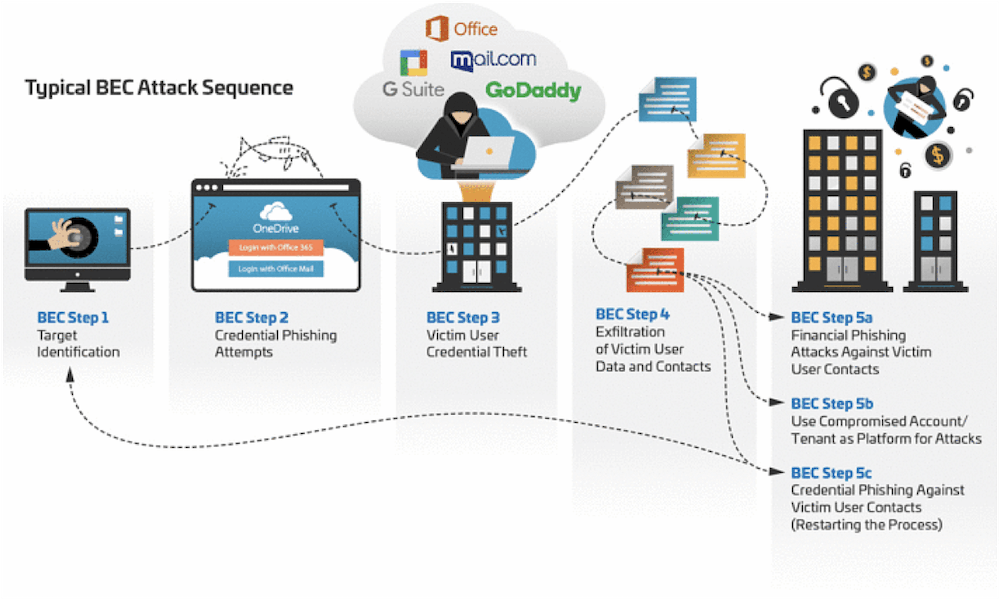
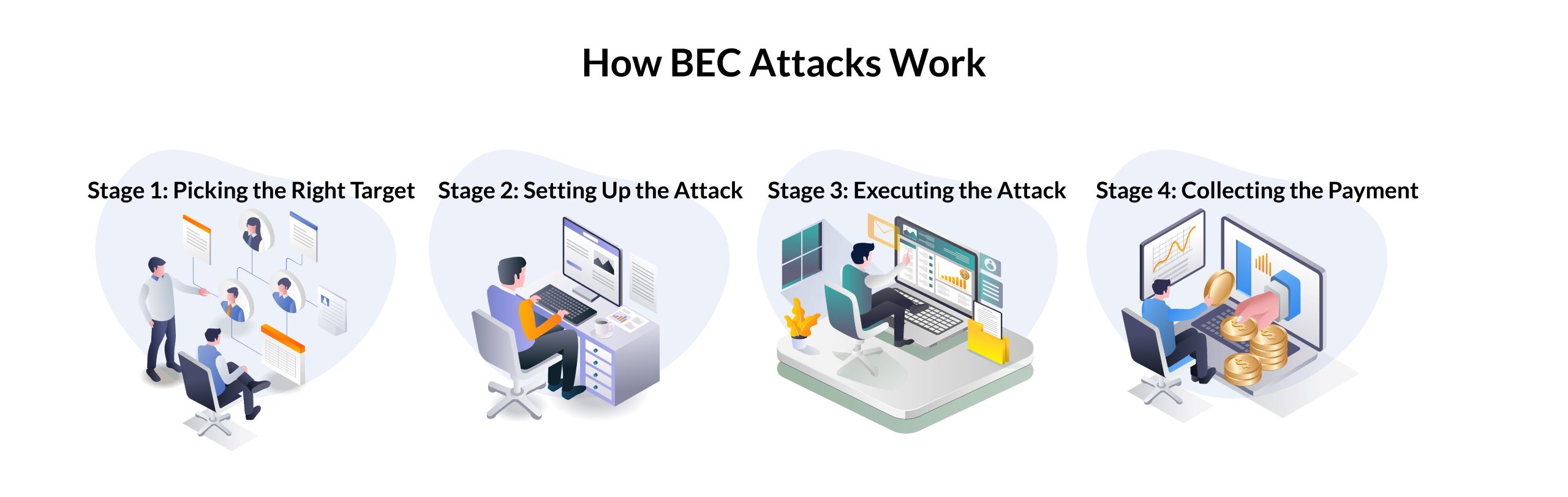


![The 10 Stages of Business Email Compromise [infographic] The 10 Stages of Business Email Compromise [infographic]](https://blog.twinstate.com/hs-fs/hubfs/Blog/In%20Blog%20Images/infographic_BEC%20(bottom%20image).png?width=856&name=infographic_BEC%20(bottom%20image).png)



.png)
